3 Steps to Protect Construction Companies from Cyber Attacks
In the recent past, global companies like Target, Equifax and Marriot have suffered devastating cyber breaches that resulted in financial distress for the companies and many customers, as well as loss of consumer trust. While these brand names have become synonymous with cyber attacks, every organization, big or small, is subject to the same risk. In fact, a recent Forrester survey found that more than 75 percent of respondents in the construction, engineering and infrastructure industries experienced a cyber incident in the last year. This highlights the enormous exposure that construction companies face as cyber criminals seem to improve their ability by the day to penetrate company networks.
If you own or operate a construction company, you really must prepare for every form of cyber attack to the best of your ability. It’s likely that 100 percent of your organization runs on technology, so practically speaking, your construction company is also a technology company. While technology improves efficiency, it is also a gateway for the exploitation of vulnerabilities in your network. Every organization must take all reasonable steps to protect sensitive data for its business, employees and customers.
The methods used to perpetrate cyber crime are continually evolving, so it may seem like an overwhelming task to keep up-to-date on protecting your data. While a best practice is to engage a trusted partner that specializes in cybersecurity, there are three practical steps your organization can take now to strengthen your security posture. Each involves the interwoven fabric of your people, processes, and technology.
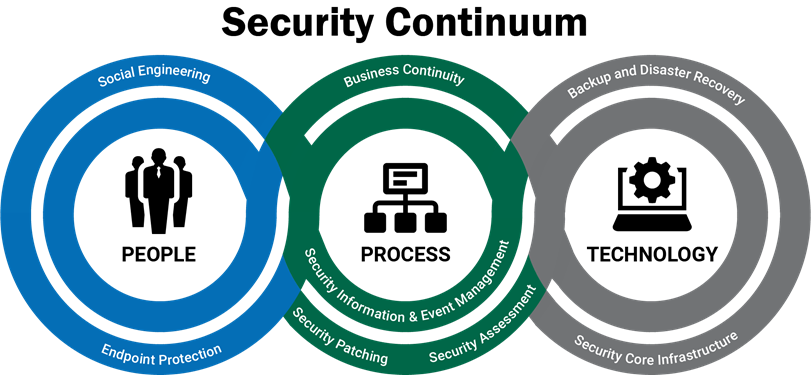
Step One: Train Your People
According to the “Cost of a Data Breach Study,” a fourth of all cyber breaches are traceable to human error. Such errors can result from a variety of actions including clicking on an infected email link or not securing sensitive information properly. It is vital to ensure that employees only have access to the information they need. For example, only select administrators should have administrative rights, and not every employee needs access to personally identifiable information. It is also essential to have proper document storage and destruction policies—and to ensure that employees know and utilize them. These steps help ensure that, should a bad actor penetrate a layer of security, the information they want most is secured and not easily accessible.
Phishing also is a common method hackers use as a way to enter into an organization’s network. Hackers send legitimate-looking emails that may have a link or attachment that contains malware such as ransomware that takes over the device and network or encrypts your data once a user clicks on it. This form of attack is becoming more sophisticated and harder to detect. Conducting ongoing social engineering testing for your employees can help educate them and prepare them to spot these emails and identify employees who may need further training.
Step Two: Adjust Your Processes
The construction industry faces unique challenges and opportunities given its mobile workforce. Employees may operate at different sites or on the road which requires a great deal of mobile communication. In these cases, it’s crucial to select and apply appropriate mobile device management tools and processes to your company devices or employee devices in a Bring Your Own Device (BYOD) environment. For example, you may benefit from being able to wipe sensitive, business and customer data off devices remotely when those devices are no longer needed, are lost, stolen or an employee leaves the company.
In situations where data is passing through multiple devices in many locations, it is important to make sure the data is being transferred securely and ends up only in the right hands. Deploying multifactor authentication ensures that the use (or misuse) of valid usernames and passwords is not sufficient to gain access to your critical systems and data. You must also be in possession of a known, personalized device. Should a hacker steal a username and password, the hacker would also need to steal that device as well or he/she would not be able to gain access to the data.
Step Three: Maintain and Upgrade Your Technology
Making sure your people and processes are efficient and diligent will greatly improve your organization’s security posture; but attention to your technology is the third leg that cannot be overlooked. Every company should assess if it has proper security patches in place and a process to monitor that. Have you analyzed the robustness of your firewall? Does your company have a backup and recovery plan? More importantly, do you practice it? Applications, software and devices that are out-of-date also present a security risk as the manufacturer may no longer support them or deploy the necessary ongoing security patches. For example, do you still use Windows 7 on your workstations? Or Windows 2008 on your servers? These will be “End of Life” in January 2020. Software such as this must be upgraded on all devices to mitigate the risk of bad actors just waiting to take advantage of such an unsupported system. Plan your migration now.
It is a necessity for businesses, regardless of size or industry, to protect their data and customers’ data. There are many steps your organization can take today to address security with your people, processes and technology. A comprehensive assessment is the most responsible way to discover where you are today and make sure you address every area of security. Engage with a trusted partner to assess and reveal where your vulnerabilities are and what steps and budget you need to address and fix areas of weakness. This process should be ongoing and part of your annual review, as the preventive measures needed for strong cybersecurity are constantly changing. Given the climate of risk, and the importance of data to your construction business, cybersecurity must be top of mind and part of your ongoing planning. Engaging in an assessment is a good first step toward meeting your responsibility to your company, employees and customers in making security a priority.



















