Applying Lessons Learned from the Payment Card Industry Across Your Organization
By Mark Agulnik, Partner, Southeast IT Risk & Assurance Services Practice Group Leader

Payment cards have consistently been at the top of the list of the most frequently stolen types of data sources. With a number of tools used to extract data now readily available on the internet, hackers have developed complex systems to monetize stolen card information. This is why it is critical for companies to understand the risks as well as how to protect cardholder data.
The Payment Card Industry Data Security Standard (“PCI DSS” or “the Standard”) is an information security standard and applies to all entities that store, process or transmit cardholder data. The standard consists of six control objectives and twelve requirements. Below is a high level overview:
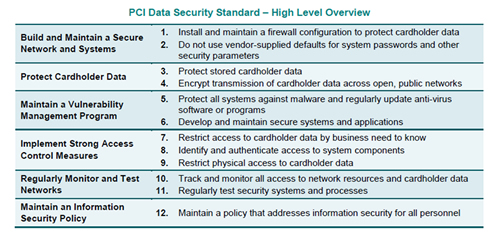
Although the standard applies to the cardholder environment, there are a significant number of requirements that should be implemented by all entities, regardless of whether they are required to comply with PCI DSS Standard. Below are a few examples.
1) Implement a Risk Assessment
The standard (requirement 12.2) requires an entity to implement a risk assessment at least annually or upon a significant change to the environment. Examples of major changes include mergers/acquisitions or changes to significant systems. A risk assessment enables an organization to identify threats and associated vulnerabilities that can negatively impact an entity. Once the likelihood and impact of the threat is determined, an entity should then determine how to address this risk.
International Organization for Standardization (ISO) 31000:2009 provides the following methods for managing risk:
- Avoiding the risk by deciding not to start or continue with the activity that gives rise to the risk.
- Accepting or increasing the risk in order to pursue an opportunity.
- Removing the risk source.
- Changing the likelihood.
- Changing the consequences.
- Sharing the risk with another party or parties (including contracts and risk financing).
- Retaining the risk by informed decision.
Examples of widely used risk assessment methodologies include but are not limited to OCTAVE, ISO 27005 and NIST SP 800-30.
2) Screen Potential Personnel and Train Employees on Security Policies and Procedures
The standard (requirement 12.7) emphasizes the importance of screening potential personnel prior to hire to minimize the risk of attacks from internal sources. Procedures include performing background checks including previous employment history, criminal record, credit history, and reference checks. It is especially important to conduct rigorous background checks for technology employees (e.g., network administrators, help desk, etc.), as many of these specialists will receive elevated credentials which can allow them to access an entity’s assets for unauthorized and malicious purposes.
The standard (requirements 12.6 and 12.6.1) also requires that the entity implement a formal security awareness program to make all personnel aware of the security policy and procedures. Training related to security policies should be conducted upon hire and at least annually. If personnel are not educated about their security responsibilities, security safeguards and processes that have been implemented may become ineffective through errors or intentional or unintentional actions.
Training should be tailored based on the applicable risks of the entity. Common training topics include social engineering, phishing attacks, malware, physical security, desktop security, wireless network security and reporting a security incident. To ensure that personnel commit to complying with security policies, the standard (requirement 12.6.2) requires personnel to acknowledge at least annually that they have read and understood the security policy and procedures.
3) Implement Strong Access Controls
The standard (Requirement 7) states that critical data and systems should only be accessed by authorized personnel based on a “Need to Know” basis. Therefore, personnel should have access to the least amount of data needed to perform the job. The more access provided, the more risk that information will be used maliciously. The most effective way to determine the extent of access is by assigning access based on the individual’s job classification and function (Requirement 7.1.3). An entity should have documented approval for an employee’s level of privilege, which can assure that access and privilege are known and authorized by management.
For new roles, there should be a default “deny-all” setting and privilege should be added only as a need occurs. Entities should also ensure that if an employee changes roles (e.g., a promotion or a lateral move) that the previous privileges are assessed and disabled as necessary. It is also critical that access is revoked immediately for any terminated users (requirement 8.1.3).
There are several best practices to increase an entity’s security environment. Most important is to begin with a risk assessment and ensure proper controls over critical areas.
The PCI standard is complex in nature and every organization should ensure they are in compliance to avoid unnecessary fines and fees. For further information regarding PCI-DSS, please contact a Marcum team member.


















