How Companies Can Effectively Manage Individual Privacy Rights
Ensuring the privacy rights of employees, customers, clients, vendors and stakeholders is a compliance obligation that impacts businesses, organizations and institutions around the globe.
A patchwork of privacy regulations (GDPR, CCPA, SOC 2 Privacy, HIPAA/HITRUST, to name a few) have been rapidly implemented over the last few years. Yet, maintaining compliance has become a significant burden to companies. Not meeting these regulations can result in severe fines, lawsuits and reputational damage, while meeting them can require a large up-front investment (both in employee time and expenses).
If the idea of identifying, understanding and complying with varying privacy regulations in different jurisdictions seems overwhelming, there’s some comfort to take. Marcum’s Risk Advisory Services professionals assist clients of all sizes and scopes with implementing security and privacy programs. In doing so, we’ve identified a large number of overlapping principles and requirements between the frameworks. That said, your business or organization should strongly consider taking 10 key actions immediately to enhance internal privacy controls and meet regulatory requirements. These actions are briefly outlined below.
(1) Implement and enhance policies and procedures. These can and should encompass areas such as risk management, data management, application development, facility access, breach/incident response and reporting, data integrity and retention and more. The goal is to be prepared to address the full range of privacy and risk issues that impact your organization with established and consistent procedures.
(2) Implement a data inventory and mapping process. This process plays a crucial role in understanding the types of data stored, how it is collected and used, and where it is stored. It should encompass all relevant company systems and departments, including, HR, IT and Marketing.
(3) Perform a privacy impact assessment of identified data. Factors to consider throughout this process:
- The information that needs to be collected
- Why the information is being collected
- The intended use of the information
- With whom the information will be shared
- What opportunities individuals will have to provide information or to consent to particular uses of the information
- How information will be secured
- Whether a system of records is being created under the privacy policy
(4) Perform an organizational risk assessment. This should include every relevant threat event to your organization, with corresponding assessments of variables such as:
- Threat type and threat source characteristics
- Relevance/likelihood of threat initiation or occurrence
- Vulnerabilities and their relative severity
- Predisposing conditions and their relative pervasiveness
- The likelihood of success for an initiated threat
- The level of impact
- The overall risk level (high, medium, low, N/A)
(5) Implement a vendor risk management process. We recommend to clients that they develop a thorough inventory of all current vendors with access to relevant data; assess the security risk, compliance requirements, and overall impact; and obtain missing or updated confidentiality, security and other data-handling requirements, along with evidence that each vendor meets internal risk requirements. Additionally, we recommend development and deployment of processes to manage the collection and review of vendors as they are onboarded, and regularly thereafter.
(6) Develop a privacy notice and system boundaries. Your organization can create this by utilizing information learned through data inventory and mapping activities, as well as vendor lists, risk assessments and other internal resources. There are numerous pieces of information that a proper privacy notice should include. While not a comprehensive list, below are a few examples:
- How we use your personal data
- Providing your personal data to others
- International transfers of your personal data
- Amendments
- Your rights
- About cookies, and cookies we use
This notice should be posted in appropriate locations based on relevant regulatory requirements. We recommend limiting disclosures to the minimum reasonable under the requirements. Before publishing your notice, review one more time and share with relevant stakeholders to prevent any misinterpretation or inability to meet the statements outlined within.
(7) Reduce data footprint and collection. The goal here is to limit your exposure to the data you collect, process and store to only what is absolutely necessary. In doing so, it is important to determine your organization’s ability to individualize records. You should also consider implementing anonymization techniques to prevent linking private/confidential information back to the individual; stop collecting unnecessary information; and disclose the types of data the system is designed to retain.
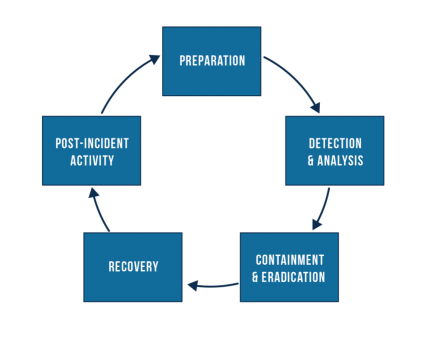
(8) Develop formal incident and breach handling/notification process. Your organization should implement a formal plan to manage incidents from identification to resolution. This includes identification of the incident; containment; eradication; recovery; and follow-up. Note that incidents that rise to the level of a breach require additional handling, including, but not limited to: investigation; risk assessment adjustments; implementation of additional logging, monitoring and alert notification software; and retraining.
(9) Implement sufficient security and privacy awareness training. Some key attributes to include:
- Define privacy and explain its importance
- Identify privacy laws, policies, guidance and principles
- Understand your role in protecting privacy and the consequences for violations
- Define personally identifiable information (PII) and list examples
- Outline how to protect PII in different contexts and formats
- Highlight how to recognize potential threats to privacy
- Describe how to report a privacy incident
Other useful training activities include social engineering exercises (e.g., phone calls and on-site, phishing exercises and table-top exercises).
(10) Implement an IT general control framework. Your organization’s framework could account for any relevant frameworks, such as, but not limited to:
- NIST SP 800-53
- ISO 27001
- HITRUST
- ISACA COBIT 5
- SOC 2
What’s the risk of not implementing these steps…of not being prepared? Well, severe fines, lawsuits and reputational damage, as highlighted earlier. But beyond these, your organization faces an uphill climb in its drive to pursue its mission, remain vital and serve its customers, clients and stakeholders. Compliance issues can be challenging; but with the right plan and processes in place, they are manageable, which allows you and your people to focus on what you do best.




















