Understanding the HIPAA Security Rule
By Christopher Denton, Manager, Risk Advisory
If your company handles protected health care information (PHI), chances are that you’ve heard of HIPAA (the Health Insurance Portability and Accountability Act). Although discussions about HIPAA colloquially involve privacy, the HIPAA Security Rule is much more important and translates directly to IT systems.
What is the HIPAA Security Rule?
The HIPAA Security Rule applies to:
- Covered Entities (CE) – health plans, health care clearing houses, and any health care provider that transmits health information in electronic form.
- Business Associates (BA) – an individual who “creates, receives, maintains or transmits” PHI on behalf of a covered entity.
Its purpose is to require covered entities and business associates to provide protection against reasonably anticipated threats, and includes several requirements including risk analysis and management, administrative safeguards, physical safeguards and technical safeguards.
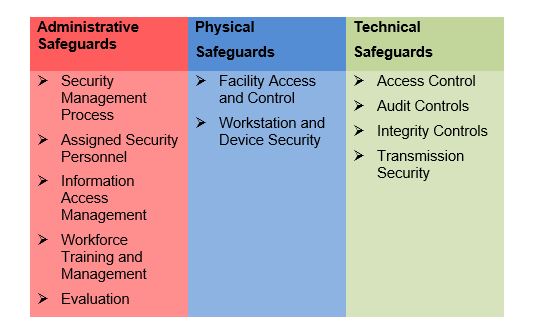
The Security Rule has two different types of implementation standards—required and addressable. The CE or BA must implement any standards marked as required. For addressable standards, the CE or BA must implement the standard if appropriate—or if not, document why it would not be reasonable and appropriate to implement the standard. The Security Rule also requires that covered entities and business associates periodically assess how well their security policies and procedures meet the requirements of the Rule.
How do I become compliant?
The Security Rule does not suggest how the standards must be implemented, but instead allows the CE or BA to choose controls and solutions based on their size and resources.
- Step 1 – the first step to becoming compliant is conducting a gap analysis and risk assessment. Knowing where your risk lies and how ePHI could be breached will allow you to implement policies and controls to mitigate that risk.
- Step 2 – a HIPAA Security or SOC 2 examination will provide assurance that the Security Rule is being met on an ongoing basis.
- Step 3 – continuous risk assessment as new technology, software and systems are added or removed will enable your organization to better avoid data breaches.
Do you need to make sure your organization is compliant with a gap analysis or risk assessment? Interested in learning more about HIPAA Security, SOC 2 examinations or other risk advisory matters? Contact your Marcum representative at (855) MARCUM1.




















