Weak Password and Security Guidelines Put Patient Health Records at Risk

The issues around patient data security are many – the message simple; the need to constantly consider the electronic threats to your data has never been greater. Many of our clients have done their checking on a regular basis and find that there are periodic lapses in procedures or in installation of “patches”. The bottom line is you need to make sure your IT integrity is always up to date. Call us if you need to get some help.
Federal agency monitoring EHR certification leaves door open to hackers by not requiring the use of strong passwords and other safety standards
Published Date: August 8, 2014
By Lisa Smith
Strong passwords are the first line of defense against computer hackers. But a government report warns that patients are at risk because the certification process for electronic health records (EHRs) doesn’t require the use of a strong password.
An audit by the U.S. Department of Health and Human Services’ Office of Inspector General (OIG) takes issue with the criteria used by the Office of the National Coordinator for Health Information Technology (ONC) to certify EHR vendors.
“Our audit revealed vulnerabilities with the Temporary EHR certification program,” said the report. “These vulnerabilities could allow hackers to penetrate EHR systems, thereby compromising the integrity, confidentiality, and availability of patient information stored in and transmitted by a certified EHR.”
The OIG noted that the acceptance of a single character password for certification was inadequate and pointed to the need for more complex passwords.
The ONC currently deputizes private bodies, known as Authorized Testing and Certified Bodies (ATCBs), to certify that records meet defined minimum technology standards in seven information technology areas: access control, emergency access, automatic log-off, audit log, integrity,authentication, and general encryption. The agency also defines the criteria for the certification process.
The ONC responded that the temporary process was no longer active and that its 2014 certification criteria had “strengthened test procedures for common security and privacy features for inclusion in EHRs,” but the OIG says that the 2014 criteria still did not address common security issues, such as password complexity and/or logging emergency access or user privilege changes.
Since 2009, 32 million Americans have had their medical records compromised, according to an HHS website. Some of the breaches resulted from employee carelessness, but many point directly to password vulnerabilities and encryption issues.
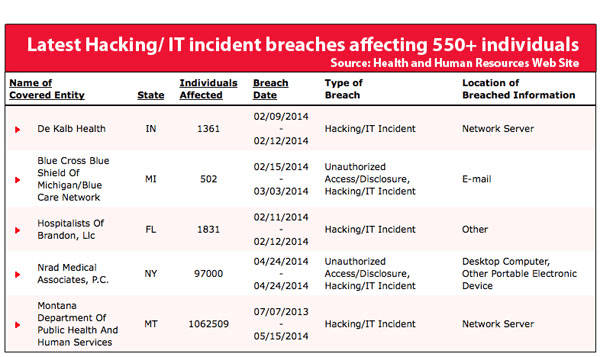
Large-scale cyber breaches of personal records, such as the recent hacking of 1.2 billion user names and passwords from 420 companies, are becoming more frequent. Medical records are an even more attractive target then financial records, according to Politico, because they contain enough information to build a full identity, worth $500 on the black market.
The Affordable Care Act requires that all public and private healthcare providers and other eligible professionals (EPs) adopt and demonstrate meaningful use of electronic health records beginning January 1, 2014 to maintain their existing Medicaid and Medicare reimbursement levels.
A key factor is that providers can’t use noncertified EHR software to attest to meaningful use.
There are financial incentives for healthcare providers who prove meaningful use of EHRs, and penalties for non-compliance. EPs who haven’t implemented EHR systems and demonstrated their meaningful use by 2015 will experience a 1% reduction in Medicare reimbursements, with rates of reduction likely to rise annually thereafter.
In addition to incentives and penalties for EHR adoption, EPs also might have difficulty using the ICD-10 coding system outside of an EHR system.
As a result, EHR adoption is at a record high. A National Center for Health Statistics (NCHS) survey found 78% of office-based doctors used an EHR system in 2013, up from 72% in 2012 and 57% in 2011. The number of solo practitioners and small practices who had adopted electronic health record systems (EHRs) jumped to 61% in 2014, up from 50% in 2013.
But adopters are looking to the government for assistance in making sure records are safe, a fact noted in the OIG report.
“The process of certifying EHRs is designed, in part, to give providers the confidence to know that patient health information is secure and protected,” OIG stated. Government guidance is especially crucial because many healthcare organizations and EPs have little awareness of the risks associated with health information technology, according to a report prepared by RAND Health and the ONC.
“Health IT safety often competes with other pressing priorities for limited resources within healthcare organizations,” the ONC wrote in a blog post. “It also tells us that users of electronic health records (EHRs) see EHRs as a solution to patient safety problems, and may not understand new risks that may be introduced by EHRs.”
The large-scale rollout of EHRs comes as hackers are increasingly exploiting vulnerabilities like weak passwords to gain access to personal information. In 2012, 749,000 people’s data were stolen by Eastern European hackers due to a weak password policy. The list of victims include recipients of Medicaid and a health care program for low-income children in Utah, officials at Utah’s Department of Health said in a statement. Hackers were able to breach the servers by exploiting a technician’s weak password.
“ONC’s baseline does not address certain specific security concerns and industry best practices,” the OIG audit noted. “Therefore, we continue to recommend that ONC strengthen EHR Test Procedure requirements to address such issues to ensure providers have EHR systems that have adequate security and privacy features.”
Source: Medical Economics



















