PCI DSS 4.0 – Vulnerability Assessment and Penetration Testing Changes
The Payment Card Industry Data Security Standard (PCI DSS) has remained in version 3 since 2013, with new clarifications and additional guidance issued every couple of years to address identified gaps but without a major overhaul. PCI DSS 4.0 is that comprehensive overhaul. Officially released as of Q1 2022, it was designed to mitigate current and future security risks given the dynamic growth of threats and technology in the marketplace. Specifically, PCI DSS 4.0 is designed to achieve four primary goals:
- Continue to meet the security needs of the payment industry.
- Promote security as a continuous process.
- Add flexibility for different methodologies.
- Enhance validation methods.
Following the release of 4.0, there is two-year window (through March 31, 2024) for entities that store, process, and/or transmit cardholder data to have their controls aligned with the primary requirements 4.0 introduces, followed by one additional year (March 31, 2025) to implement the future-dated requirements, some of which will be discussed within. This article focuses on changes that impact controls related to the performance of vulnerability assessments and penetration testing, along with a few honorable mentions.
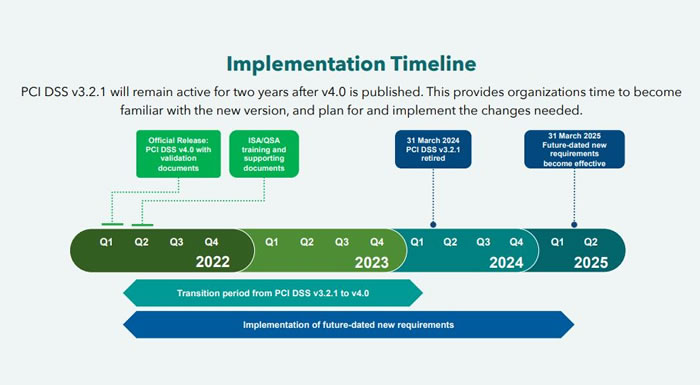
Figure 1: https://www.pcisecuritystandards.org
What’s Changing with Vulnerability Assessments and Penetration Testing?
These requirements are getting a much-needed facelift, including solidifying some of the weaker requirements that were more than likely permitted as half-measures given the major technology changes required of covered entities.
First, vulnerability assessments are becoming slightly more invasive, now requiring companies to perform authenticated scanning. This is probably something that should have been required in the past; however, many organizations are concerned with the performance impact these scans sometimes bring. Additionally, internal network risks of medium and lower severity identified through vulnerability scanning will now also need to be managed (not necessarily remediated), where previously the focus was limited to high and critical findings.
Also new to version 4.0, requirement 11.4.1 expands the penetration testing methodology to include testing from within and outside the cardholder data environment (CDE), where previous requirements focused on the internal perimeter and optionally within the CDE. Companies will also have to better document their approach to assessing and addressing exploitable risks, and retain the results of testing for at least 12 months.
Last but certainly not least (and likely to be the most impactful of the changes), multi-tenant service providers will have to enable/allow customers to perform a penetration test on their own tenant/infrastructure or be provided a report from a third-party testing organization to support the requirement. Appendix A1 of the PCI DSS 4.0 standard further details steps organizations must take to prevent potential lapses in data access, including implementing logical separation between providers’ environments and customers’ environments and confirming this separation via penetration testing.
What’s Next?
The implementation date for most of the changes mentioned in this article won’t be until March 2025, giving everyone plenty of time to make the transition. There will be many technical/architectural and security decisions to be made, as well as budget considerations related to the expansion of testing requirements — especially for multi-tenant service providers. Marcum Technology, along with the Risk Advisory Group of Marcum LLP, are able to support all organizations in every step of their PCI journey, from gap assessment and consulting on potential solutions (process and tooling) to solving complex challenges and producing a formal Report on Compliance.
Marcum Technology provides a full cybersecurity service offering. If you need any help, from beginning a review of your security posture to investigating a cybersecurity incident, or even if you just want to ask for advice on a situation you are facing, please contact us at [email protected] #AskMarumTechnology

















