Critical Elements of a Secure Digital Transformation
By Wesam Hasan, Senior Network Engineer, Marcum Technology
Companies are recognizing that their existing technology — such as traditional router-centric enterprise WANs and perimeter-based security strategies — lack the elasticity, scalability, and agility to keep up with the most sophisticated new technology. As a result, many are embarking on a digital transformation: the process of migrating their data and business-critical applications to the cloud.
Moving applications from enterprise data centers to the cloud is a necessary component of the increasingly popular software as a service (SaaS) consumption model, which requires direct and secure access to the cloud. Furthermore, as a result of the COVID-19 pandemic more users are working remotely, and they need to securely forward data directly to the data center’s cloud applications. Another factor in the push for digital transformation is the expanding attack surface due to the evolution of mobile and IoT devices across verticals. Networks are now more vulnerable to security breaches that can result in data exfiltration and network interruption.
These changes expose the limitations of traditional network designs that have the firewall sitting at the edge of the network, as well as the need for scalable, agile, secure, and reliable solutions that can rapidly adapt to new technology needs.
With these shifts in technology implementations, network, and security, modernization is necessary to deploy and securely access applications in the cloud. This leads us to SASE, a solution that can overcome the limitations of the traditional network models.
What is SASE?
SASE, or secure access service edge, is a technology that combines networking and security capabilities. The framework consolidates network and security services as depicted in figure 1 below. This service is delivered by a cloud security platform that can provide protected access to SaaS applications and off-network users (remote or mobile). It extends security functions to remote branch locations and off-network users to provide direct, secure access to the internet and the cloud resources from anywhere and at any time.
How SASE Resolves Network and Security Challenges
SASE consolidates networking and security services, providing the following capabilities:
- SDWAN to provide a virtual WAN overlay and smart forwarding capabilities to the internet and the cloud applications.
- Firewall as a service (FWaaS) in the cloud to provide next-generation firewall (NGFW) services, including an intrusion prevention system (IPS), anti-malware, SSL inspection, and sandbox.
- A cloud access security broker (CASB) monitors all activity and enforces security policies for users and applications./li>
- A secure web gateway (SWG) protects internet-enabled devices from web-based threats including viruses, malware, and phishing.
- Web application and API security as a service (WAAPaaS) protect web-facing applications.
- Zero trust network access (ZTNA) verifies devices and users before accessing resources within the network. This includes technologies like single sign-on (SSO) and multi-factor authentication (MFA), network access control (NAC), and access policy enforcement.
- A domain name system (DNS) stops threats at the DNS layer.
With SDWAN and NGFW running at the data centers and remote branches, data traffic forwarding decisions are application-centric. This provides the ability to send internet traffic to a cloud-delivered security platform for advanced inspection and then forward the traffic to a SaaS or IaaS in the cloud. An advanced SD-WAN platform uses a virtual WAN overlay to enforce end-to-end micro-segmentation. It also enables application-based QoS to prioritize business-critical applications. Figure 1 below shows how the technology works.
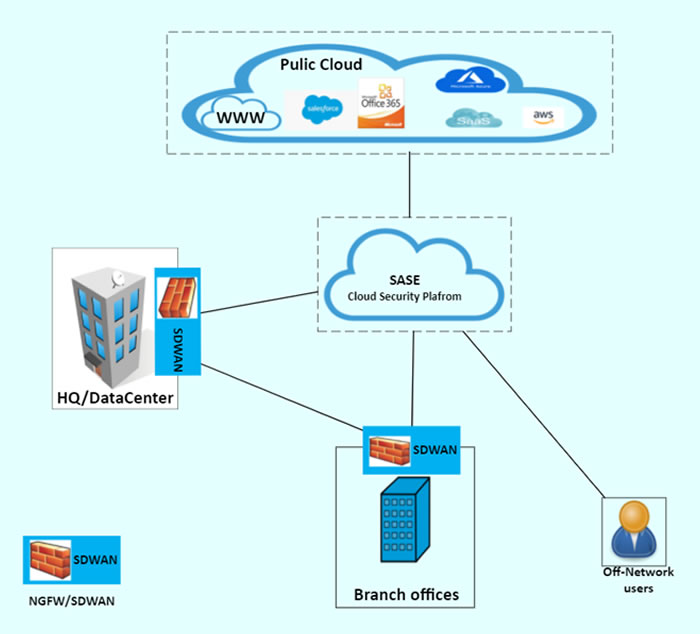
Figure 1: SASE topology, with NGFW/SDWAN, the branches and remote/mobile users can make forwarding decisions directly to the cloud.
As mentioned previously, SASE combines network and security functions. This combination provides an end-to-end, software-defined network and security overlay to achieve the following:
- Lowest latency and best performance to access SaaS applications.
- Elastically delivered solutions to rapidly scale as needed.
- Security for off-network users.
- Unified security and policy enforcement across the board.
- Combined security and network services and management.
- Fully meshed redundant paths to internet and cloud resources.
WAN Modernization
To truly benefit from digital transformation, users need fast, reliable, and secure access to the network and data in the cloud, from anywhere (on- or off-network). To support an as-a-service model, enterprises need a secure cloud access platform that can scale elastically to connect the remote sites and off-network users to the cloud resources and data centers.
However, traditional WAN infrastructures hinder the digital transformation process. That’s because traffic from remote sites and remote users is backhauled to the data centers. The traffic is then forwarded to the cloud applications or the internet. As a result, bandwidth bottlenecks and network devices throughput issues become an obstacle in the data center. Dynamic failover and uptime can also overcomplicate the network design.
In summary, a few common obstacles with traditional WANs can hinder digital transformation:
- High cost.
- Complexity and scalability limitations.
- Bandwidth and throughput bottlenecks.
- Lack of end-to-end traffic visibility.
- High latency when accessing cloud applications.
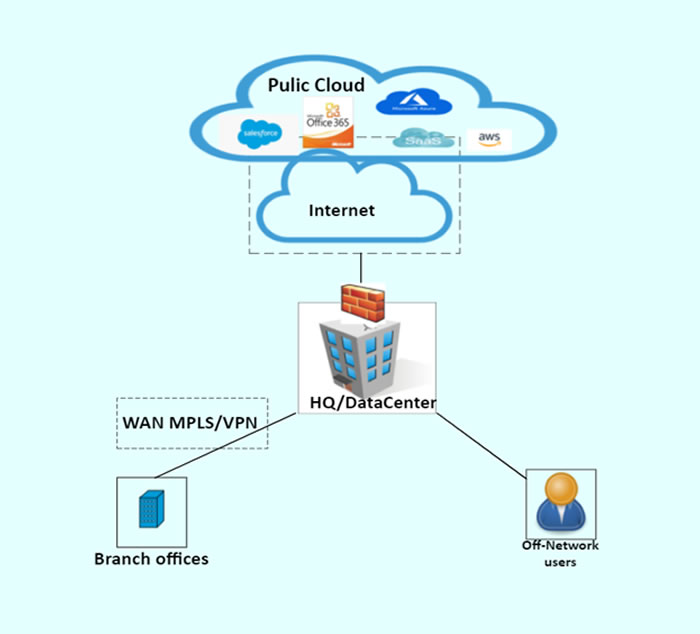
Figure 2: Traditional WAN design
Cybersecurity Considerations
As new cybersecurity threats rise exponentially and become more and more sophisticated, and as more users work from anywhere, at any time, there is increasing concern around off-network usage and the increase in attack surface for bad actors.
It is becoming extremely difficult for traditional security solutions to scale up and protect businesses and user data. Threat hunting operations are overwhelming tasks for InfoSec and SOC teams. In addition, it can be difficult to maintain compliance requirements while increasing network nodes and platforms —consider retail businesses that are required to be PCI compliant when new applications are hosted in the cloud and will be accessed by thin clients that are installed on machines located in small retail locations.
Items to consider that impact network security:
- Increased attack surface.
- Off-network users impact security policy enforcement.
- New cybersecurity threats and compliance challenges.
- Traffic inspection/visibility and its impact on cloud applications’ performance.
Adopting a SASE solution is not an easy task, whether you’re choosing the right SASE provider or configuring QoS and security policies. Here at Marcum Technology, we have experienced consultants who are ready to engage throughout the entire process and deliver a customer-specific SASE solution. For more information, contact [email protected] #AskMarcumTechnology




















